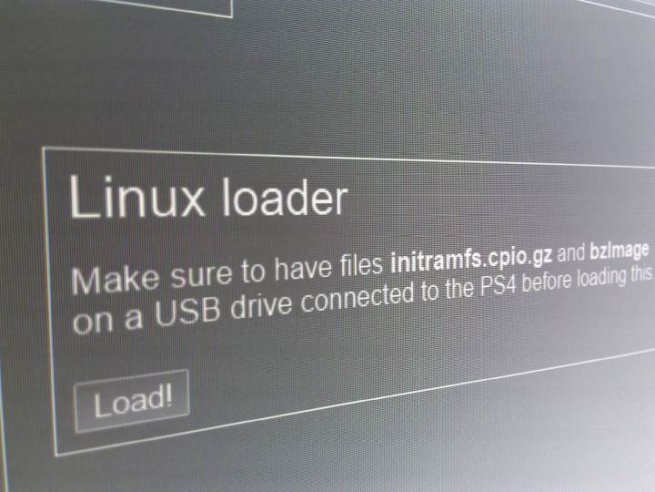
il faut avoir accès à l'exploit webkit de Cturt tout simplement

.
Pourquoi rester sur un firmware inférieur sachant que tout est fait pour le 1.76, un peu comme pour le 3.55 sur PS3 en gros.
Mais je ne pense pas que l'exploit 1.76 puisse tourner sur firmware inférieur car il faut l'exploit bowser découvert sur ce 1.76.
Si tu es sur un firmware inférieur je pense qu'il faut passer sur 1.76 ( à confirmer ) .
https://cturt.github.io/ps4.html
WebKit entry point
WebKit is the open source layout engine which renders web pages in the browsers for iOS, Wii U, 3DS, PS Vita, and the PS4.
Although so widely used and mature, WebKit does have its share of vulnerabilities; you can learn about most of them by reading Pwn2Own write-ups.
In particular, the browser in PS4 firmware 1.76 uses a version of WebKit which is vulnerable to CVE-2012-3748, a heap-based buffer overflow in the JSArray::sort(...) method.
In 2014, nas and Proxima announced that they had successfully been able to port this exploit to the PS4's browser, and released the PoC code publicly as the first entry point into hacking the PS4.
This gives us arbitrary read and write access to everything the WebKit process can read and write to, which can be used to dump modules, and overwrite return addresses on the stack, letting us control the Program Counter (for ROP).
Since then, many other vulnerabilities have been found in WebKit, which could probably allow for module dumping and ROP on later firmwares of the PS4, but as of writing, no one has ported any of these exploits to the PS4 publicly.
If you have never signed into PSN, your PS4 won't be able to open the Internet Browser, however you can go to "Settings", and then "User's Guide" to open a limited web browser view which you can control the contents of with a proxy.