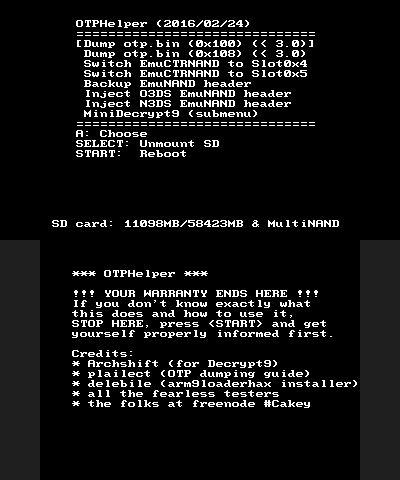
This is what this can / should do:Dump the OTP.bin (0x100 or 0x108)On-the-fly switching of the CTRNAND crypto slot 0x4 -> 0x5 or slor 0x5 -> 0x4Dumping the NCSD NAND headerInjecting the NCSD NAND headerIncludes a basic set of Decrypt9WIP functionality, including...... dumping / injecting the cryptoswitched CTRNAND partition!This is what needs testing:Duming the NAND header on O3DS (not dangerous!)OTP Dumping, cryptoswitching, injecting the NAND headerDumping / injecting the cryptoswitched CTRNAND partition The code is rather simple, so I'm pretty sure we won't need a whole lot of testing, but i still need to refine some stuff until this can have a proper release.WARNING:This has not been sufficiently tested. Parts of it are not tested at all (because testing these parts require a hardmod for safety). Don't use this, at least not for injecting the EmuNAND dump into SysNAND, if you don't have a NANDmod!(This text will be reworded after some testing has taken place).!TESTERS NEEDED!This is what needs testing:Dump the OTP.bin (0x108 bytes at best) and compare it with the output of one of the already tested OTP dumpers. Is the file identical? Only works < FW 3.0 of course.(N3DS only) After the downgrade to 2.x, switch your EmuCTRNAND to slot 0x4 (instead of using the two XORpads, 3DSFAT16Tool and the NAND backup for that). Does it work as intended?(N3DS only) According to the above, upgrade your system to a version >= 9.x and switch back to slot 0x5 (upgrade might not work though).Try the backup EmuNAND header function on O3DS - does it work and do you get a valid header dump?(N3DS only) Try the inject EmuNAND header functions - do they work as intended?